Category
Forensics
Chall Author
MSAB
Stats
Total Solves: 6/20 Teams
Final Points: 380p
Description
We’ve captured a suspected flag stealer and extracted their phone. We suspect they have hidden the stolen flag in their Whatsapp backup. Can you help us find it?
Solution
In the challenge you were given a zip file with the Whatsapp backup for an Android phone. The first thing I found suspicious was that most of the files in the .zip file had a .crypt15 extension. And after a quick Google search I found that this is one of Whatsapp’s encryption methods for their databases, especially backups.
After some more googling I found that a 64 character long backup key was required to decrypt the .crypt15 files. Time to search!
After some searching in the file system I found a nice directory:
phone_root\root\data\com.whatsapp\databases
There I found an unencrypted sqlite3 .db file “msgstore.db”. Within the table “message” I found 3 messages.
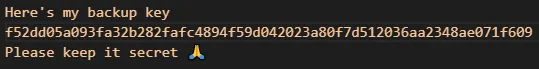
Now that I have found the backup key, I can decrypt the .crypt15 files and thus find more clues or maybe the flag. The first step was of course to google🙏, where after a little searching I found this nice tool:
https://github.com/ElDavoo/wa-crypt-toolsSince I found the backup key in msgstore.db and that there is a db file named "msgstore.db.crypt15" I wanted to decrypt this first.
python -m pip install wa-crypt-toolsAfter decryption, all you had to do was open the new "msgstore.db" and enter the table messages, which shows these chat logs:
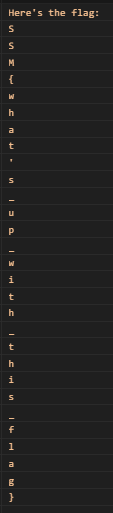
Flag
SSM{what's_up_with_this_flag}